Apple M-Series Chips’ New “GoFetch” Vulnerability Exposes Secret Encryption Keys

Apple M-series semiconductors contain a new security flaw that could be leveraged to extract secret keys needed for cryptographic operations. The vulnerability, dubbed GoFetch, is related to a microarchitectural side-channel attack that targets constant-time cryptographic implementations and retrieves sensitive data from the CPU cache by utilizing a data memory-dependent prefetcher (DMP) feature. The results were […]
Differences Between the Encryption Algorithms of DSA, ECC, and RSA?

RSA, DSA, and ECC encryption algorithms are the primary algorithms used for generating keys in public key infrastructure. Public key infrastructure (PKI) is used to manage identity and security in internet communications and computer networking. The core technology enabling PKI is public key cryptography, an encryption mechanism that relies upon the use of two related keys, […]
Apple is being sued by the US Justice Department for monopoly and messaging security.

The U.S. Department of Justice (DoJ), along with 16 other state and district attorneys general, on Thursday accused Apple of illegally maintaining a monopoly over smartphones, thereby undermining, among other things, the security and privacy of users when messaging non-iPhone users. “Apple wraps itself in a cloak of privacy, security, and consumer preferences to justify its anticompetitive […]
The most effective method to pick the right kind of database.

Attempting to select a database? Learn about the various kinds of databases and how to choose the best one by using this guide. Understanding the diverse types of databases and their specific use cases is crucial for selecting the right database for your project. I’ve been working on some detailed course material to help people […]
Kubernetes: Unleashing the Power of Container Orchestration
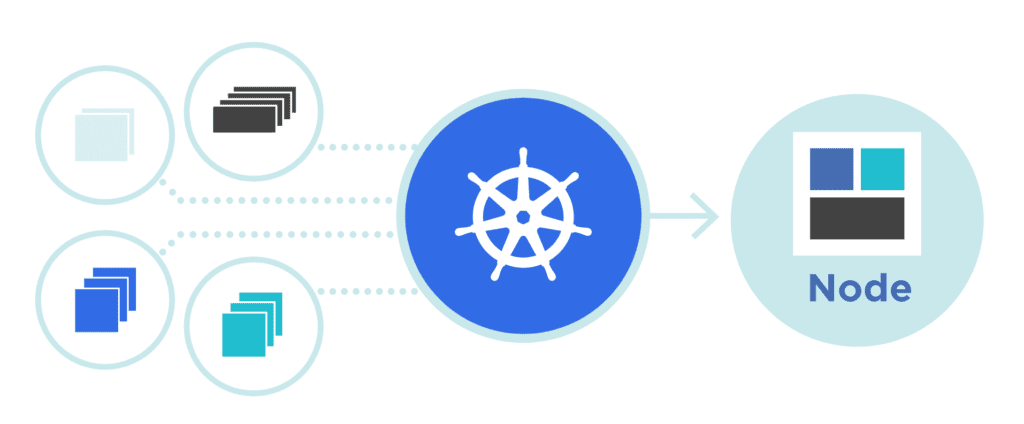
As the heartbeat of modern cloud-native applications, Kubernetes is not just some tech jargon—it’s a powerhouse tool transforming the way IT operates. If you’re a techie navigating through the intricate networks of IT infrastructures or an organization aiming to streamline its deployments, Kubernetes is on your radar. But what’s behind the hype? This extensive dive […]
Navigating the Cloud: A Comprehensive Guide to Public Cloud Migration Services

In today’s dynamic business landscape, where agility, scalability, and innovation are paramount, the adoption of cloud computing has become a cornerstone of digital transformation strategies. Among the various cloud deployment models, the public cloud stands out for its accessibility, scalability, and cost-efficiency. Public cloud migration services serve as the bridge that enables organizations to transition […]
Air-gapping: Is This Something Your Organization Should Consider?

In today’s digital age, cybersecurity has become a top priority for businesses of all sizes. With the increasing number of cyber threats and data breaches, companies are constantly looking for ways to protect their sensitive information. One method that has gained popularity is air-gapping. Air-gapping is a security measure that involves physically isolating a computer […]
Understanding the Importance of Good Database Design
Database design is a critical aspect of any software development project. Whether you are building a small application or a complex enterprise system, the quality of your database design can greatly impact the performance, scalability, and maintainability of your application. So, what exactly is good database design? In simple terms, it refers to the process […]
Understanding Watering Hole Attacks: Threats, Prevention, and Protocols

Introduction Watering hole attacks have become an increasingly prevalent threat in the digital landscape. In this blog post, we will explore the nature of watering hole attacks, the protocols used to carry out these attacks, and the prevention measures that organizations can take to protect themselves. What is a Watering Hole Attack? A watering hole […]
Understanding Social Engineering: Tactics, Risks, and Prevention

Introduction Social engineering is a deceptive technique used by cybercriminals to manipulate individuals into revealing sensitive information or performing actions that could compromise their security. It involves exploiting human psychology and trust to gain unauthorized access to systems or data. Tactics Used in Social Engineering There are several tactics that social engineers employ to deceive […]





